The ‘Zelle Fraud’ Scam: How it Works, How to Fight Back
One of the more common ways cybercriminals cash out access to bank accounts involves draining the victim’s funds via Zelle, a “peer-to-peer” (P2P) payment service used by many financial institutions that allows customers to quickly send cash to friends and family. Naturally, a great deal of phishing schemes that precede these bank account takeovers begin with a spoofed text message from the target’s bank warning about a suspicious Zelle transfer. What follows is a deep dive into how this increasingly clever Zelle fraud scam typically works, and what victims can do about it.
Last week’s story warned that scammers are blasting out text messages about suspicious bank transfers as a pretext for immediately calling and scamming anyone who responds via text. Here’s what one of those scam messages looks like:
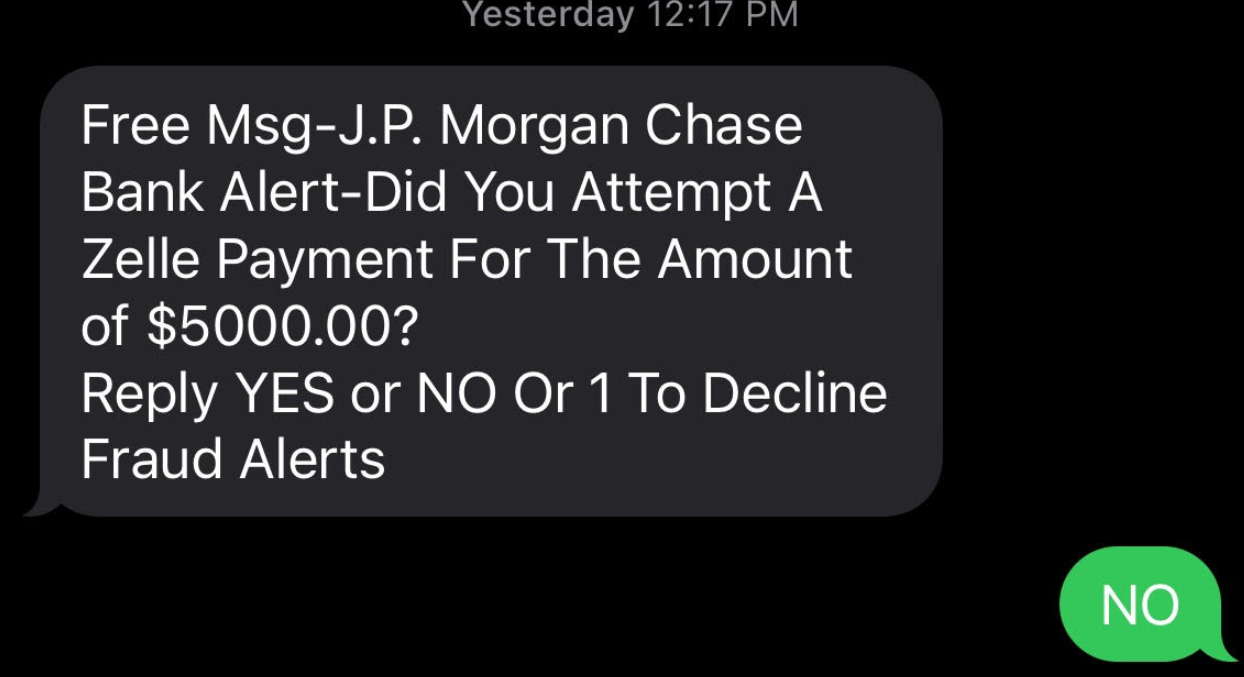
Anyone who responds “yes,” “no” or at all will very soon after receive a phone call from a scammer pretending to be from the financial institution’s fraud department. The caller’s number will be spoofed so that it appears to be coming from the victim’s bank.
To verify the identity of the customer, the fraudster asks for their online banking username, and then tells the customer to read back a passcode sent via text or email. In reality, the fraudster initiates a transaction — such as the “forgot password” feature on the financial institution’s site — which is what generates the 2-step authentication passcode delivered to the member.
Ken Otsuka is a senior risk consultant at CUNA Mutual Group, an insurance company that provides financial services to credit unions. Otsuka said a phone fraudster typically will say something like, “Before I get into the details, I need to verify that I’m speaking to the right person. What’s your username?”
“In the background, they’re using the username with the forgot password feature, and that’s going to generate one of these two-factor authentication passcodes,” Otsuka said. “Then the fraudster will say, ‘I’m going to send you the password and you’re going to read it back to me over the phone.'”
 The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.
The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.
An important aspect of this scam is that the fraudsters never even need to know or phish the victim’s password. By sharing their username and reading back the one-time code sent to them via email, the victim is allowing the fraudster to reset their online banking password.
Otsuka said in far too many account takeover cases, the victim has never even heard of Zelle, nor did they realize they could move money that way.
“The thing is, many credit unions offer it by default as part of online banking,” Otsuka said. “Members don’t have to request to use Zelle. It’s just there, and with a lot of members targeted in these scams, although they’d legitimately enrolled in online banking, they’d never used Zelle before.” [Curious if your financial institution uses Zelle? Check out their partner list here].
Otsuka said credit unions offering other peer-to-peer banking products have also been targeted, but that fraudsters prefer to target Zelle due to the speed of the payments.
“The fraud losses can escalate quickly due to the sheer number of members that can be targeted on a single day over the course of consecutive days,” Otsuka said.
To combat this scam Zelle introduced out-of-band authentication with transaction details. This involves sending the member a text containing the details of a Zelle transfer – payee and dollar amount – that is initiated by the member. The member must authorize the transfer by replying to the text.
Unfortunately, Otsuka said, the scammers are defeating this layered security control as well.
“The fraudsters follow the same tactics except they may keep the members on the phone after getting their username and 2-step authentication passcode to login to the accounts,” he said. “The fraudster tells the member they will receive a text containing details of a Zelle transfer and the member must authorize the transaction under the guise that it is for reversing the fraudulent debit card transaction(s).”
In this scenario, the fraudster actually enters a Zelle transfer that triggers the following text to the member, which the member is asked to authorize: For example:
“Send $200 Zelle payment to Boris Badenov? Reply YES to send, NO to cancel. ABC Credit Union . STOP to end all messages.”
“My team has consulted with several credit unions that rolled Zelle out or our planning to introduce Zelle,” Otsuka said. “We found that several credit unions were hit with the scam the same month they rolled it out.”
The upshot of all this is that many financial institutions will claim they’re not required to reimburse the customer for financial losses related to these voice phishing schemes. Bob Sullivan, a veteran journalist who writes about fraud and consumer issues, says in many cases banks are giving customers incorrect and self-serving opinions after the thefts.
“Consumers — many who never ever realized they had a Zelle account – then call their banks, expecting they’ll be covered by credit-card-like protections, only to face disappointment and in some cases, financial ruin,” Sullivan wrote in a recent Substack post. “Consumers who suffer unauthorized transactions are entitled to Regulation E protection, and banks are required to refund the stolen money. This isn’t a controversial opinion, and it was recently affirmed by the CFPB here. If you are reading this story and fighting with your bank, start by providing that link to the financial institution.”
“If a criminal initiates a Zelle transfer — even if the criminal manipulates a victim into sharing login credentials — that fraud is covered by Regulation E, and banks should restore the stolen funds,” Sullivan said. “If a consumer initiates the transfer under false pretenses, the case for redress is more weak.”
Sullivan notes that the Consumer Financial Protection Bureau (CFPB) recently announced it was conducting a probe into companies operating payments systems in the United States, with a special focus on platforms that offer fast, person-to-person payments.
“Consumers expect certain assurances when dealing with companies that move their money,” the CFPB said in its Oct. 21 notice. “They expect to be protected from fraud and payments made in error, for their data and privacy to be protected and not shared without their consent, to have responsive customer service, and to be treated equally under relevant law. The orders seek to understand the robustness with which payment platforms prioritize consumer protection under law.”
Anyone interested in letting the CFPB know about a fraud scam that abused a P2P payment platform like Zelle, Cashapp, or Venmo, for example, should send an email describing the incident to BigTechPaymentsInquiry@cfpb.gov. Be sure to include Docket No. CFPB-2021-0017 in the subject line of the message.
In the meantime, remember the mantra: Hang up, Look Up, and Call Back. If you receive a call from someone warning about fraud, hang up. If you believe the call might be legitimate, look up the number of the organization supposedly calling you, and call them back.
from Krebs on Security https://ift.tt/3xcZO5S


Comments